webapp for looking at and searching through log files
Project description
Tailon is a self-hosted web application for looking at and searching through log files. It is little more than a fancy web wrapper around the following unix commands:
tail -f tail -f | grep tail -f | awk tail -f | sed
Tailon is under development.
Screenshots

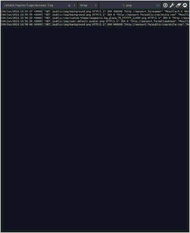
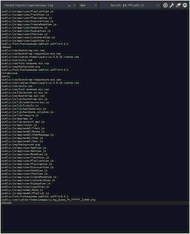
Installation
The latest stable version of tailon is available on pypi, while the development version can be installed from github:
$ pip install tailon # stable version
$ pip install git+git://github.com/gvalkov/tailon.git # development versionAlternatively, it can be installed manually:
$ git clone git@github.com:gvalkov/tailon.git
$ cd tailon
$ git reset --hard HEAD $versiontag
$ python setup.py installUsage
To get started with tailon you only need to point it to the files that you wish to see in the web interface:
$ tailon -f /var/log/nginx/* /var/log/apache/{access,error}.logOnce this is done, visit http://localhost:8080 with your browser.
Tailon’s server-side functionality is succinctly documented in its help message:
$ tailon --help
Usage: tailon [-c path] [-f path [path ...]] [-h] [-d] [-v] [-b addr:port]
[-r path] [-a]
Tailon is a webapp for looking at and searching through log files.
Required arguments:
-c, --config path yaml config file
-f, --files path [path ...] list of files or file wildcards to expose
Optional arguments:
-h, --help show this help message and exit
-d, --debug show debug messages
-v, --version show program's version number and exit
-b, --bind addr:port listen on the specified address and port
-r, --relative-root path web app root path
-a, --allow-transfers allow file downloads
Example config file:
bind: 0.0.0.0:8080 # address and port to bind on
allow-transfers: true # allow file downloads
relative-root: /tailon # web app root path (default: '')
files:
- '/var/log/messages'
- '/var/log/nginx/*.log'
- '/var/log/xorg.[0-10].log'
- 'cron': # sub-section
- '/var/log/cron*'
Security
Tailon runs commands on the server it is installed on. While commands that accept a script (eg. awk, sed, grep) should be invulnerable to shell injection, they may still allow for arbitrary command execution and/or access to the filesystem. To clarify, the following sed script - 's/a/b';cat /etc/passwd' - will result in an error as the command is not invoked through a shell. On the other hand, r /etc/passwd is a perfectly valid sed script that has the same effect as the above attempt for a shell injection.
The default set of enabled commands - tail, grep and awk - should be safe to use. Awk is ran in sandbox mode, which prevents scripts from accessing your system (either through the system() builtin or through input redirection).
Similar Projects
Attributions
tailon’s favicon was created from this icon.
License
Tailon is released under the terms of the New BSD License.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.











