Extract and aggregate IOCs from threat feeds.
Project description






An extendable tool to extract and aggregate IOCs from threat feeds.
Integrates out-of-the-box with ThreatKB and MISP, and can fit seamlessly into any existing worflow with SQS, Beanstalk, and custom plugins.
Overview
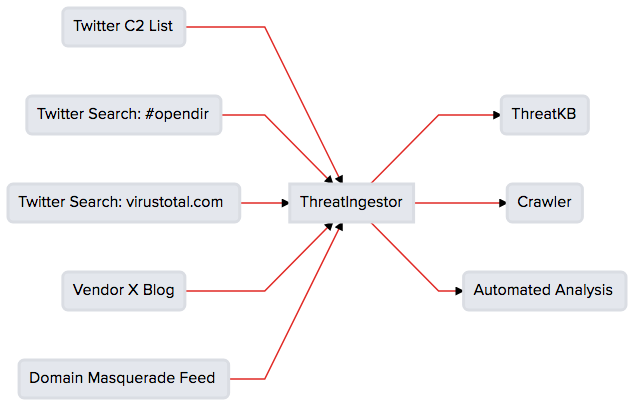
ThreatIngestor can be configured to watch Twitter, RSS feeds, or other sources, extract meaningful information such as malicious IPs/domains and YARA signatures, and send that information to another system for analysis.
Try it out now with this quick walkthrough, or see more ThreatIngestor walkthroughs on the InQuest blog.
Installation
ThreatIngestor requires Python 3.6+, with development headers.
Install ThreatIngestor from PyPI:
pip install threatingestor
Install optional dependencies for using some plugins, as needed:
pip install threatingestor[all]
View the full installation instructions for more information.
Usage
Create a new config.yml file, and configure each source and operator module you want to use. (See config.example.yml for layout.) Then run the script:
threatingestor config.yml
By default, it will run forever, polling each configured source every 15 minutes.
View the full ThreatIngestor documentation for more information.
Plugins
ThreatIngestor uses a plugin architecture with “source” (input) and “operator” (output) plugins. The currently supported integrations are:
Sources
Operators
View the full ThreatIngestor documentation for more information on included plugins, and how to create your own.
Threat Intel Sources
Looking for some threat intel sources to get started? InQuest has a Twitter List with several accounts that post C2 domains and IPs: https://twitter.com/InQuest/lists/c2-feed. Note that you will need to apply for a Twitter developer account to use the ThreatIngestor Twitter Source. Take a look at config.example.yml to see how to set this list up as a source.
For quicker setup, RSS feeds can be a great source of intelligence. Check out this example RSS config file for a few pre-configured security blogs.
Support
If you need help getting set up, or run into any issues, feel free to open an Issue. You can also reach out to @InQuest on Twitter.
We’d love to hear any feedback you have on ThreatIngestor, its documentation, or how you’re putting it to work for you!
Contributing
Issues and pull requests are welcomed. Please keep Python code PEP8 compliant. By submitting a pull request you agree to release your submissions under the terms of the LICENSE.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Hashes for threatingestor-1.0.0b6-py2.py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | b45c9d448a2cf1bed14a0d325607e9fc4fc1a0dc9b5f2601ad2be703eba6ba99 |
|
| MD5 | f6030d2be0f8a1877b0cb9edcfe2b1b2 |
|
| BLAKE2b-256 | 93a9b8d36c257800e81f7918a0f299f786390f6a5630dec93b5464dc4d56602e |











